On the 16th February, the Joint Cyber Security Centre (JCSC) held a webinar on “Identifying Australia’s Threat Landscape'', with special guest Jonathan Horne CEO of .au registrar, Terrific and cyber security firm, Cyber Aware. Jonathan provided guidance on how leaders can foster change within the workplace through understanding data, identifying risks and making improvements.
Understanding data
Jonathan began by explaining what the team at Cyber Aware strives to do: to help businesses understand and improve their cybersecurity culture through focused training programs and phishing simulations. They use a unique dataset established to perform a cybersecurity health check with questions assessing controls in place within the organisation (i.e. network and wi-fi security, email security, disaster recovery etc).
Through analysis, he explained, the team is able to pinpoint specific areas for improvement and identify underrepresented risks facing the wider Australian business community. One of these risks, he went on, is an absence of Multi-Factor authentication (MFA), also referred to as 2 Factor-Authentication (2FA), a technique used to protect online accounts through an additional verification mechanism, such as by sending a code via SMS to a mobile phone before access to an online account is granted. He told us that cyber criminals are looking to identify soft targets and launch attacks on organisations that have gaps in their cybersecurity strategies, explaining his “back to basics” approach and offering the below advice:
“Cybersecurity doesn't need to be complicated. Doing simple things like 2 Factor Authentication that cost very little can have a significant impact on reducing your organisation's risk.”
Identifying risks
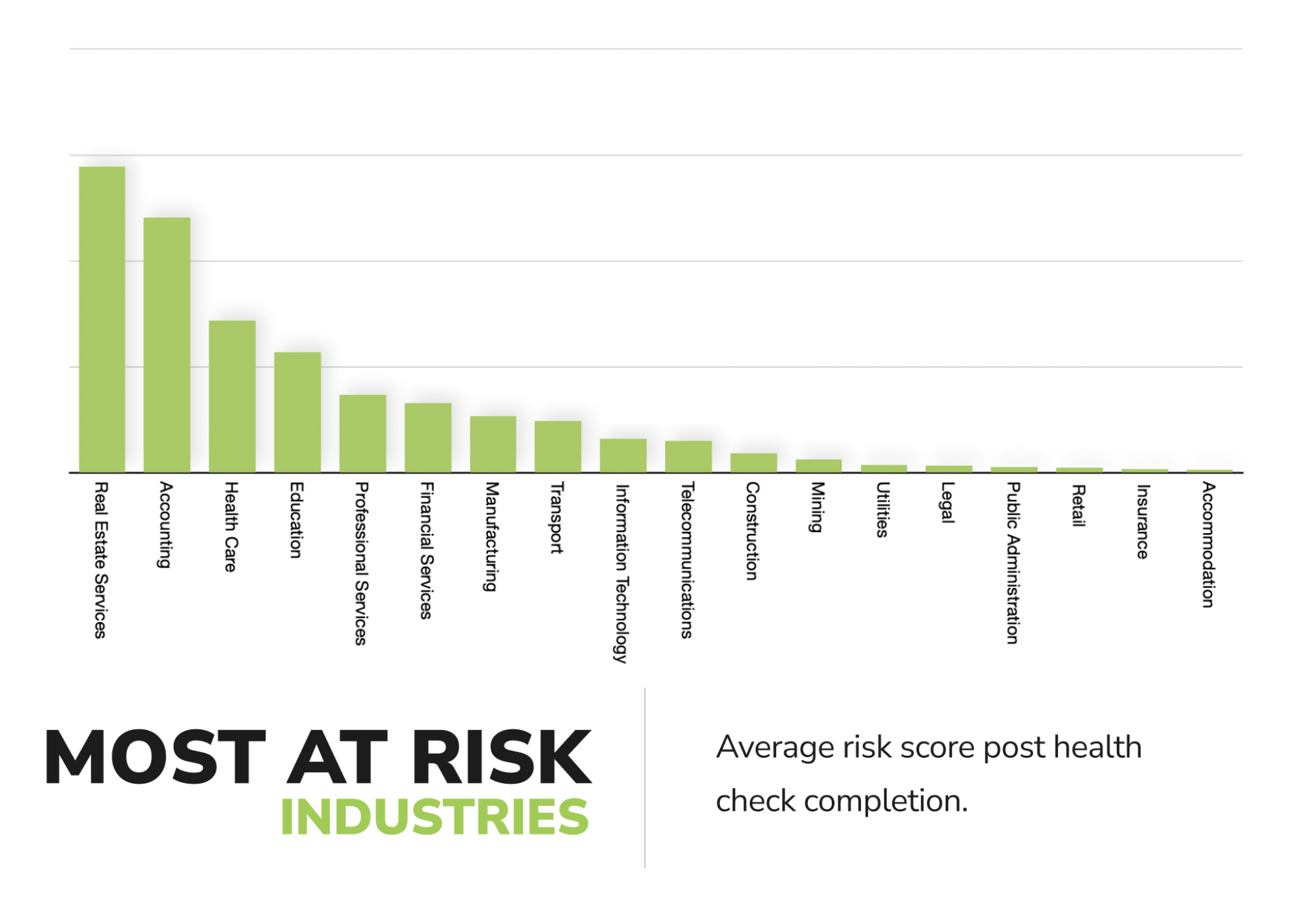
Jonathan revealed that the 3 industries at the highest risk for cybersecurity exploits in Australia are:
- Real estate;
- Accounting and;
- Healthcare.
Image 1: Industries most at risk of cybersecurity exploits
However, he also suggested that cybercriminals are not particularly fussy and attempt to exploit organisations regardless of industry, which is why he stresses the importance of keeping on top of your cybersecurity strategy and awareness at all times.
An alarming fact that Jonathan shared was that employees are often targeted as a result of their accessibility and lack of cybersecurity knowledge. Often, the main entry point for a phishing or social engineering exploit (e.g. when the attacker sends an email pretending to be a senior representative of the organisation) is a new or inexperienced employee. The email usually requires the recipient to click on a link/download an attachment to access a form for a payment to be made. Once the link is clicked on or the form has been downloaded, these criminals have access to the organisation’s systems which may take some time for the organisation to become aware of.
Making improvements
Once risks and weaknesses have been identified, recommendations from Cyber Aware are likely to focus on ensuring the organisation is following highly regarded security practices, such as The Australian Cyber Security Centre’s Essential 8. As a list of mitigation strategies which make it more difficult for adversaries to compromise systems, The Essential 8 presents a baseline security model and includes information on why enhancements such as patching, running frequent backups, restricting security privileges and implementing Multi- Factor authentication are critical.
Once these enhancements are in place, organisations should look at improving soft controls, such as employee knowledge, which can be done through regular training and updates. Jonathan reminded us that employees should be constantly reminded of cybersecurity risks, whether it’s through workplace posters, online training, frequent discussion and/or imitation phishing campaigns.
Jonathan wrapped up by emphasising that the focus for business leaders needs to remain on improving the cybersecurity culture. Cybersecurity awareness should frequently be discussed in conversation, during meetings — at any time of collaboration — to make sure it remains front of mind for all employees. Jonathan stressed that frequency and engagement is key to maintaining a low human risk score and in benefiting the overall cybersecurity posture of an organisation.
Here at Afilias Australia we understand the critical impact of maintaining a prominent cybersecurity culture which is why we conduct regular security training for staff to help ensure that our support of .au domain names is as secure as possible. In addition to complying with the Essential Eight, a host of other security precautions such as 2FA and limited access controls are in place to ensure the security and stability of the .au namespace.
If you would like more information on improving cybersecurity within your business contact Jonathan Horne at jonathan@cyberaware.com.au or to get in touch with us please email blog@afilias.com.au.